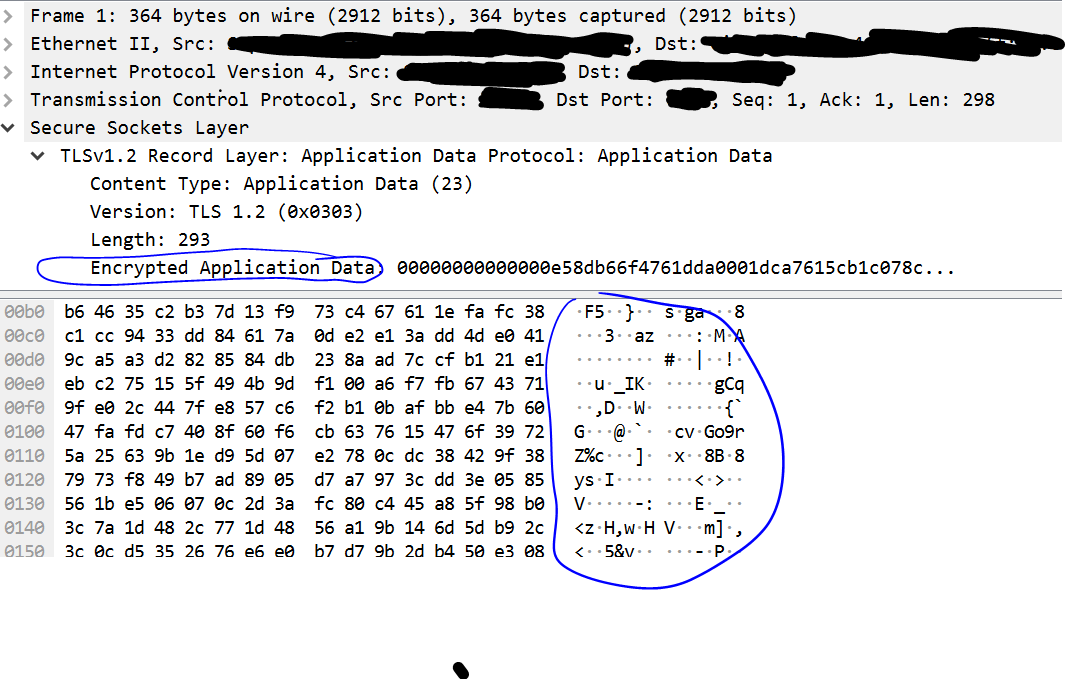
tcpdump and wireshark
To capture traffic from my rsyslog encryption exercise and ensure the traffic was encrypted, I used tcpdump on the server, and wireshark on my local machine.
tcpdump -nnvvvS -s 0 -U -w /tmp/<capture file name> -i <interface> dst <destination IP> and dst port <port number>
tcp dump helpfully counts packets for you, so when I had several I turned off tcpdump (ctrl-C), and moved my capture file to my local machine, and opened it up in wireshark.